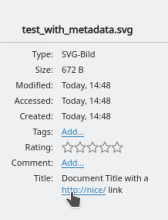
Properties from arbitrary sources may contain any character, also
valid Qt richtext (HTML subset) sequences. In best case, this only
causes parsing and display issues, but may also inject malicious links:
<a href="http://malicous.domain/">unconspicious</a>.
The originUrl value is not affected, as QUrl percent-encodes '<' and '>',
thus can not contain any HTML tags. Explicitly cast the originUrl
QVariant to QUrl, which is always valid for values coming from KFileMetadata.
This affects all versions prior to 19.08.00. D21470 accidentally disabled
interactive links in the labels, thus malicious links are disabled.
Depends on D25239