This adds a new body part formatter plugin for application/pgp-keys mime type and application/vnd.gnupg.wks mimetype.
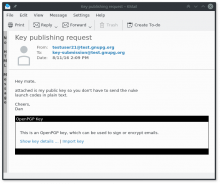
The application/pgp-keys formatter simply prints a message saying that this is an OpenPGP key and explains what that is, as seen below:
User can click the "Show key details" link to get details about the key (uid, creation date, fingerprint), and if the key is available in local keyring there will also be "Open in Kleopatra" link.
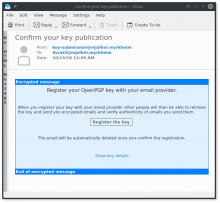
The application/vnd.gnupg.wks mimetype formatter handles the WKS Publishing Confirmation request. The request is worded in the terms of "Registration", which might be better for the user, and has a button to "Register".
Once clicked, the formatter silently sends the confirmation response to WKS and deletes both the request and the response.