For the development Project EasyGPG we would like to see better support for Opportunistic encryption in Kmail.
Currently (I've checked with 4.14) there is the option in "Securtiy -> Composing -> Automatically encrypt messeges whenever possible" I think we can reuse that option and improve it.
With this option enabled KMail shows a Dialog on send:
It's a Dialog and thus an extra click and it is not transparent what happens when you click send.
Also KMail currently only does a keylisting which would not automatically fetch a Key even if "auto-key-retrieve" is enabled in GnuPG. When auto-key-retrieve is enabled in the GnuPG System the retrieval should also happen when composing a mail. This will automatically add support for "more trusted" key directories like the proposed Web Key directory:
http://www.ietf.org/id/draft-koch-openpgp-webkey-service-00.txt
Or other new Key Directories GnuPG might support in the future. The API to use for this is GnuPG's locate-keys command. Though this currently returns a list of all the keys found for a mailbox. I've talked to GnuPG upstream about this and In the future GnuPG will provide API to ask for a single "best" key (upstream issue https://bugs.gnupg.org/gnupg/issue2359 ). For now I'll implement that resolution in libkleo. I'll ping in this issue when It's done.
I imagine it to work this way as a first step (we can of course discuss it):
- When opening a new composer encrypt is initially unselected even if an encryption key is selected for this identity.
- Once a mailbox is entered KMail starts a "Locate Keys" command for this mailbox.
- When this is finished and a Key with at least Unknown Validity for this UID is found KMail toggles the Encrypt action and shows the "This message will be encrypted" Status.
- Signing is taken from the Identity configuration "Automatically Sign Messages" just as now.
- If a mailbox is added for which no key can be found and encrypt was toggled automatically encrypt is untoggled.
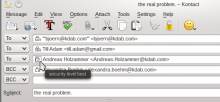
To indicate for which mailboxes keys were found there could be a status indicator next to the mail like:
This indicator shows the validity of the key. There are six levels. In Kleopatra I've used the following mapping as status Icons for some mockups / Ui work in the signencfiles-3 branch:
switch (uid.validity()) {
case UserID::Ultimate:
case UserID::Full:
return QIcon::fromTheme(QStringLiteral("emblem-favorite"));
case UserID::Marginal:
return QIcon::fromTheme(QStringLiteral("emblem-success"));
case UserID::Never:
return QIcon::fromTheme(QStringLiteral("emblem-error"));
case UserID::Undefined:
case UserID::Unknown:
default:
return QIcon::fromTheme(QStringLiteral("emblem-information"));
}There should probably also be an icon or "waiting" indicator if the locate-keys command does not return quickly.
For KMail we will need new Icons that have some crypto indication. Emblem information for unknown / undefined because this indicates "You have a Key but you have no information that the key really belongs to the User ID". If a key was obtained through the Web Key Service it will probably start out with Marginal trust. In a first iteration we can probably just use two icons next to each other, actions/gpg and the emblems above.
The tooltip should indicate the validity.
In the future and if the TOFU trust model is used there will be five additional states that further define the "marginal" validity TOFU will provide. But I'll leave TOFU Support for another task as there is no GpgME API for this currently.
If the icon is clicked Kleopatra's certificate details dialog should be shown. For now this can work through a process call to kleoptra like it's already done in the messageviewer.
Sending should work the same as now. e.g.
- If send is triggered before the locate-keys command was finished the usual "Certificate selection" dialog is opened.
- If "Always show the encryption keys for approval" is selected the dialog is shown, otherwise the located keys are used.